一个由埃及亚历山大大学的学生俱乐部MSP Teach Club组织的CTF比赛,办得不错。第一次参加外国的CTF比赛,感觉出题的有些思路跟国内真是不一样。由于运维难度比赛主办没出PWN和WEB的题:D.最后还是有几道题没做出来,看各种大神全做完也是很心累。
Reverse Engineering
RE1:Gifted
一个32位ELF,运行要求输入flag。strings一下直接出结果。非常符合题目名。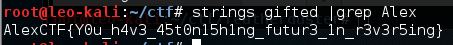
RE2:C++ is awesome
64位ELF文件,跟题目描述一样是由c++写的。拖到ida里F5一下,主要流程在400B89h处
第35行将输入与flag对比,通过在6020C0h的字符串和6020C0h处的数组选出flag
得到结果: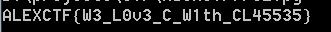
RE3:Catalyst system
64位ELF文件,运行之后要求输入一个用户名一个密码。很可恶的是出题人在输入之前和之后加了两个随机的延时,每次输入和等结果都要很久。看起来出题人是想要选手静态分析。拖入ida,F5。400C9Ah为主要流程函数。
sub_400C9A和sub_4008F7检查输入格式.
sub_400CDD中得到三个等式:
v4 - v3 + v2 == 1550207830
v3 + 3 (v2 + v4) == 12465522610
v2 v3 == 3651346623716053780
解方程组之后得到正确用户名 catalyst_ceo
sub_400977比较关键,用户名分三段相加后作为rand的种子,之后rand()生成10次,每次再与固定数值相加判断与输入密码是否相等,从这一段可以得出正确密码,通过用户名生成的种子写一段c程序生成正确密码
得到结果为
56534c73763451704763334b385779575a694136776767686a42484c4339786d567073526a676747
由于小端方式存储,反向。得密码
734c5356705134764b336347577957383641695a686767774c48426a6d783943527370564767676a
sLSVpQ4vK3cGWyW86AiZhggwLHBjmx9CRspVGggj
之后通过与保存的数组异或得到真正的flag,由于出题人的延时,这一步也自己动手。最后得到flag:
ALEXCTF{1_t41d_y0u_y0u_ar3gr34treverser__s33}
RE4: unVM me
这个题估计出题人没想过现在一堆做的很完善的py反编译工具会自动改magic number结果成了超简单的一道题。
题给了一个pyc文件,直接找个在线的pyc反编译,得到python代码
这几个MD5都是五位的可以爆破,但是有cmd5一类的网站就又省下不少时间,轻松得到flag
ALEXCTF{dv5d4s2vj8nk43s8d8l6m1n5l67ds9v41n52nv37j481h3d28n4b6v3k}
RE5: packed movement
没做出来的一道题
Being said that move instruction is enough to build a complete computer, anyway move on while you can.
拿到文件发现加过upx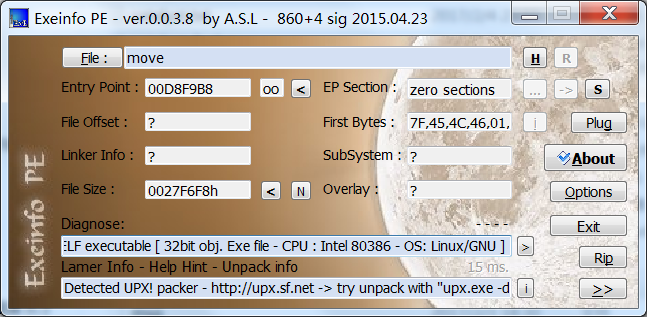
先脱掉upx,脱壳之前2M多,脱完壳9.82M,看着都吓人。拖到ida里一看,全是mov。到这就没思路了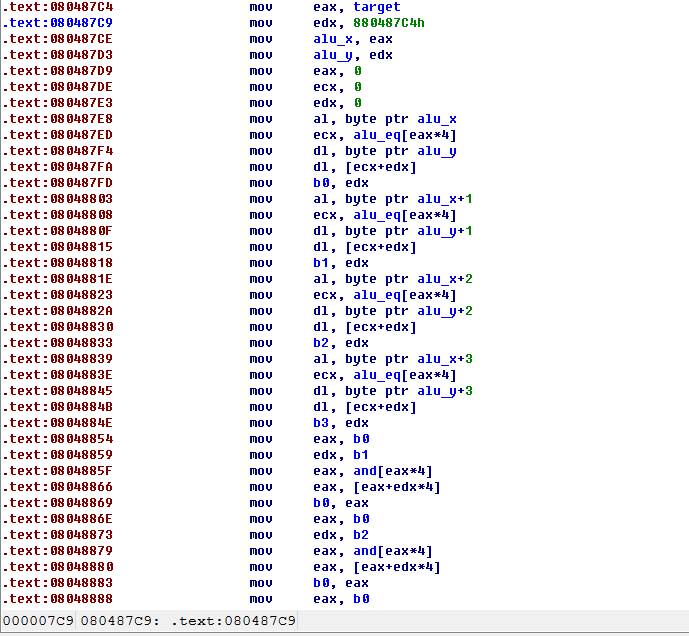
结束之后看大神writeup,发现这是由一个混淆工具处理的结果 movfuscator 看起来效果还不错,接下来主要有三种解法
搜索内容
脱完壳之后,根据flag里面有”ALEXCTF{“字符串,即0x41 0x4c 0x45 0x58 0x43 0x54 0x46 0x7b。
搜索单个字符,发现一个共同点就是mov到的地址,搜索这个地址0x8062068。
得到flag:ALEXCTF{M0Vfusc4t0r_w0rk5_l1ke_m4g1c}
大神的WP
demovfuscator + Perf
大神的WP
pass
intel-pin
大神的WP
pass
Cryptography
CR1: Ultracoded
题目给了个文件内容都是ZERO和ONE,应该是二进制,替换成01之后输出字符串发现base64编码过。
base64解码之后得到Morse码
.- .-.. . -..- -.-. - ..-. - …. .—- ….. — .—- … — ….. ..- .–. …– .-. — ….. . -.-. .-. …– - — - -..- -
再解码得到:
alexctfth15o1so5up3ro5ecr3totxt
各种改格式提交各种不对,最后发现按词义分析一下:
alexctf this o is o super o secret o txt
得到flag:
AlexCTF{th15_1s_5up3r_5ecr3t_txt}
CR2: Many time secrets
0529242a631234122d2b36697f13272c207f2021283a6b0c7908
2f28202a302029142c653f3c7f2a2636273e3f2d653e25217908
322921780c3a235b3c2c3f207f372e21733a3a2b37263b313012
2f6c363b2b312b1e64651b6537222e37377f2020242b6b2c2d5d
283f652c2b31661426292b653a292c372a2f20212a316b283c09
29232178373c270f682c216532263b2d3632353c2c3c2a293504
613c37373531285b3c2a72273a67212a277f373a243c20203d5d
243a202a633d205b3c2d3765342236653a2c7423202f3f652a18
2239373d6f740a1e3c651f207f2c212a247f3d2e65262430791c
263e203d63232f0f20653f207f332065262c3168313722367918
2f2f372133202f142665212637222220733e383f2426386b
11段密文,题目信息给得很足明显是一次性密码本多次使用了。以前没解密过,在知乎上看到一个解释很详细的问答 传送门。
套路是由于异或(a⊕b)⊕b=a的特性
m1⊕key = c1
m2⊕key = c2
c1⊕c2 = m1⊕m2
由于ascii中大写字母0x40开头小写0x60开头,空格为0x20,所以如果两段文字中空格与小写字母异或会出现大写字母,然后得到key。
手工有点麻烦,正好有一个python写的工具FeatherDuster强的很,密文输入之后选择many times pad攻击,过一会得到了解密后的明文。发现明文里没有flag,想到密钥是flag。
ALEXCTF{HERE_GOES_THE_KEY}
CR3: What is this encryption?
p=0xa6055ec186de51800ddd6fcbf0192384ff42d707a55f57af4fcfb0d1dc7bd97055e8275cd4b78ec63c5d592f567c66393a061324aa2e6a8d8fc2a910cbee1ed9
q=0xfa0f9463ea0a93b929c099320d31c277e0b0dbc65b189ed76124f5a1218f5d91fd0102a4c8de11f28be5e4d0ae91ab319f4537e97ed74bc663e972a4a9119307
e=0x6d1fdab4ce3217b3fc32c9ed480a31d067fd57d93a9ab52b472dc393ab7852fbcb11abbebfd6aaae8032db1316dc22d3f7c3d631e24df13ef23d3b381a1c3e04abcc745d402ee3a031ac2718fae63b240837b4f657f29ca4702da9af22a3a019d68904a969ddb01bcf941df70af042f4fae5cbeb9c2151b324f387e525094c41
c=0x7fe1a4f743675d1987d25d38111fae0f78bbea6852cba5beda47db76d119a3efe24cb04b9449f53becd43b0b46e269826a983f832abb53b7a7e24a43ad15378344ed5c20f51e268186d24c76050c1e73647523bd5f91d9b6ad3e86bbf9126588b1dee21e6997372e36c3e74284734748891829665086e0dc523ed23c386bb520
题目直接给了pqe,解出d之后解密,rsa千里送分题。
CR4: Poor RSA
题给了一个公钥key.pub,一个flag.b64。公钥长度太短,解密出私钥然后解密出flag。跟上题差不多。
CR5: Bring weakness
We got this PRNG as the most secure random number generator for cryptography.
Can you prove otherwise
nc 195.154.53.62 7412
正经解法
看起来是找PRNG的漏洞,第一次见。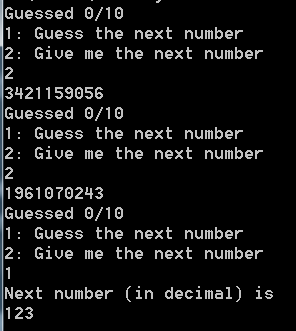
可以读数也可以猜数,猜对十个给flag。
生成伪随机数最著名的算法LCG,线性同余法。它是根据递归公式:$ x_{n+1} = ax_n +k \mod m$ ,所以第n+1个随机数是由第n个随机数和a,k,m决定的。首先求出m。
设$ t_n = x_{n+1} - x_n $,$ u_n = |t_{n+2}t_n - t_{n+1}^2| $ 。 $ m = gcd(u_1,u_2,…,u_k) $ ,m错误的概率随着k值的增大呈指数下降。
接下来求a和k,$ a = (x_{n+2}-x_{n+1})(x_{n+1}-x_n)^{-1} \mod m $,$ b = x_{n+1} - ax_n \mod m $。
求得$ m=0xffffffff, a=0x939a5ec0,k=0x8aa90086 $,通过$ x_{n+1} = ax_n +k \mod m$ 计算预测未知数,得到flag。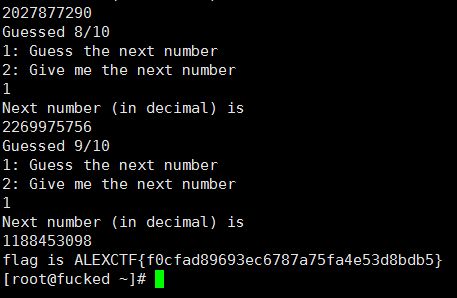
参考资料:
How to crack a Linear Congruential Generator
cracking-a-linear-congruential-generator
非正经解法
后来看到有人用别的解法,由于int型本身长度有限,直接读出一轮。具体见传送门 (因为是国外服务器,国内会偶尔连不上,想获取那么大数据量很难)
Forensics
Fore1: Hit the core
给了个coredump,但是没有程序,两眼抹黑。strings了一下只有这么一串有点意思的:
cvqAeqacLtqazEigwiXobxrCrtuiTzahfFreqc{bnjrKwgk83kgd43j85ePgb_e_rwqr7fvbmHjklo3tews_hmkogooyf0vbnk0ii87Drfgh_n kiwutfb0ghk9ro987k5tfb_hjiouo087ptfcv}
然后就卡住了,睡了一觉觉得也没啥做法只能在这上做文章试了试栅栏什么的,发现flag
cvqA
eqacL
tqazE
igwiX
obxrC
rtuiT
zahfF
reqc{
bnjrK
wgk83
kgd43
j85eP
gbe
rwqr7
fvbmH
jklo3
tews
hmkog
ooyf0
vbnk0
ii87D
rfgh
n kiw
utfb0
ghk9r
o987k
5tfb_
hjiou
o087p
tfcv}
ALEXCTF{K33P_7H3_g00D_w0rk_up}
Fore2: Mail client
题目给了一个nc地址和一个coredump文件。file一下coredump发现from mutt.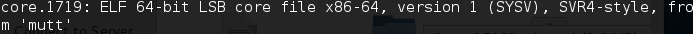 服务器交互也符合邮箱服务器。想到是取证不是pwn,判断应该是从dump文件找帐号密码。strings得到一长篇字符串,匹配@得到了一个
服务器交互也符合邮箱服务器。想到是取证不是pwn,判断应该是从dump文件找帐号密码。strings得到一长篇字符串,匹配@得到了一个
alexctf@example.com - -Mutt: (no mailbox) [Msgs:0]—(threads/date)———-(all)—
估计是邮箱帐号,接着匹配passwd发现
tp_pass = “e. en kv,dvlejhgouehg;oueh fenjhqeouhfouehejbge ef”
尝试发现不是密码,查看上下文无果。在文件中以这个密码匹配发现另一处位置,相邻有另一个字符串。!fore2 pass
尝试登陆成功,得到flag。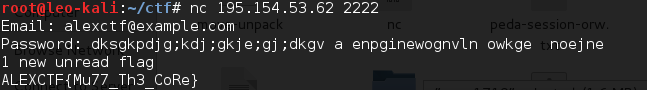
Fore3: USB probing
给了一个pcap包,wireshark打开之后发现不是之前遇到的鼠标轨迹,而是USB储存设备的数据包,把几个有数据的包中数据导出。在其中最大的包中发现PNG头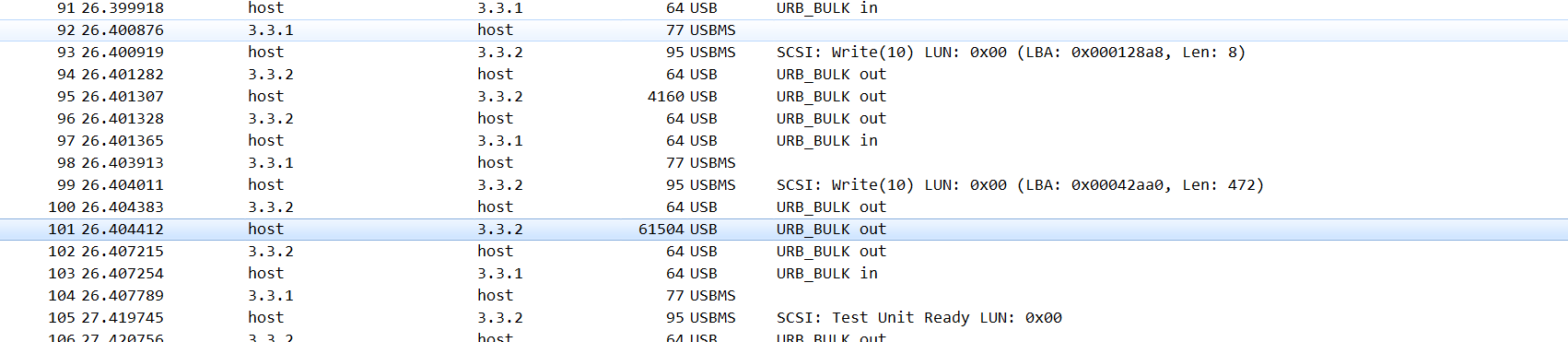
导出png用windows自带的图片查看和ps查看都是这样的
以为需要修复,但无从下手。之后在文件iTXt块中发现GIMP。用GIMP打开得到flag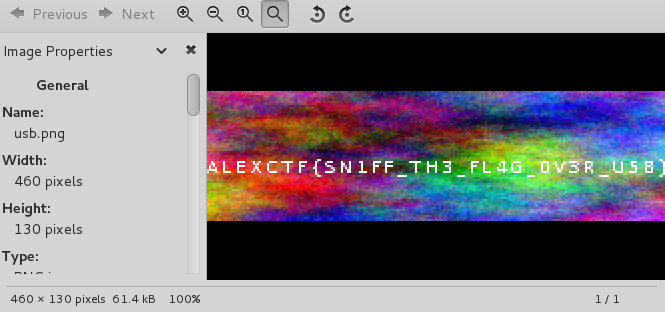
Fore4: Unknown format
跟fore3一样都是usb包,观察数据发现有个文件头是SP01,没思路。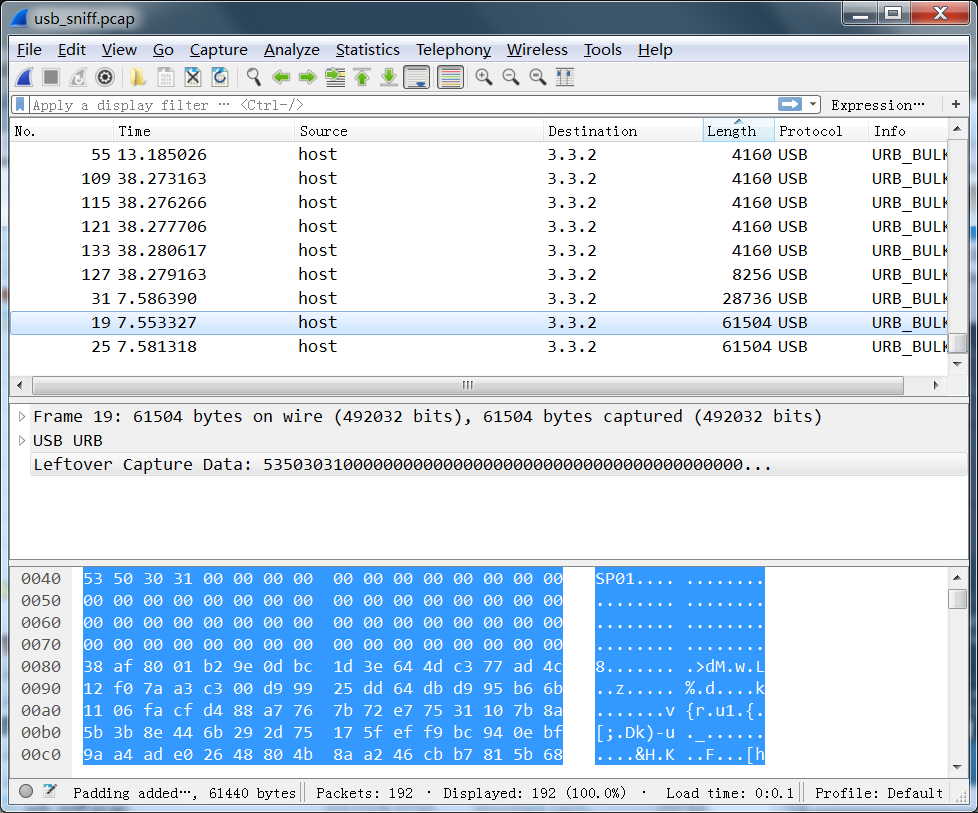
后来发现是个kindle固件,上网找到KindleTool。克隆下来编译完解出来内容,binwalk发现压缩内容,解压出来之后发现flag.txt,得到flag。
Scripting
SC1: Math bot
nc连上之后发现让算加减乘除,写脚本。开始以为100次就差不多了,结果问了500个问题才给flag。
ALEXCTF{1_4M_l33t_b0t}
SC2: Cutie cat
题目描述
yeah steganography challenges are the worst… that’s why we got only ~~one ~~ two steganography challenges .
Hint: It scripting because we need a python library to solve the challenge, one that is made in japan.
然后给了一张图片。一开始尝试几种隐写方式无果,在irc里看出题人说三行就能解决,想到了频域隐写,还各种尝试结果发现并不是。
出题人取巧做法
Hint出来之后找到了出题人用的库steganography,一行就出结果。
正经做法
上网找到原图,对比,发现异常,提取数据。具体看大佬Writeup 传送门